Both suffered from a bug where they’d fail in case the assembly to reproduce/protect didn’t have a .rsrc section. Since at the time I wrote the code all .NET assemblies had a .rsrc section, I took it for granted and didn’t include specific checks.
Tag: Phoenix Protector
Multiple Updates
A serious bug in the CFF Explorer, Rebel.NET and Phoenix Protector has been fixed. The bug affected the ExportedType .NET metadata table where the member TypeDefID was declared as a TypeDef index, while it’s a dword. The table is declared correctly in my .NET article, but somehow I wrote the wrong type in the code.
Many thanks to Yaroslav Liulko for reporting the bug.
Phoenix Protector 1.6 & Strong Name Signing
Due to the high request, I took 20 minutes of my time and updated the Phoenix Protector, bringing it to the version 1.6. The only addition to this version is the possibility to re-sign assemblies obfuscated by the Phoenix Protector.
The reason why this wasn’t possible in past version of the Phoenix Protector is that the space for the signature was removed from the assembly and the “sn.exe” tool provided by Microsoft isn’t able to re-create that space.
Now, it is possible to tell the Phoenix Protector from the options whether to remove or not the Strong Name Signature when obfuscating an assembly:
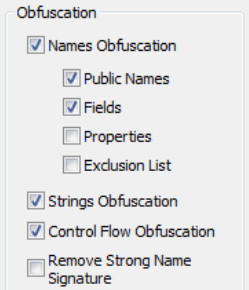
By default the Strong Name Signature is not removed.
After obfuscating anassembly, just use to re-sign the “sn.exe” tool this way:
sn.exe -R assembly.exe your_sns.pfx
